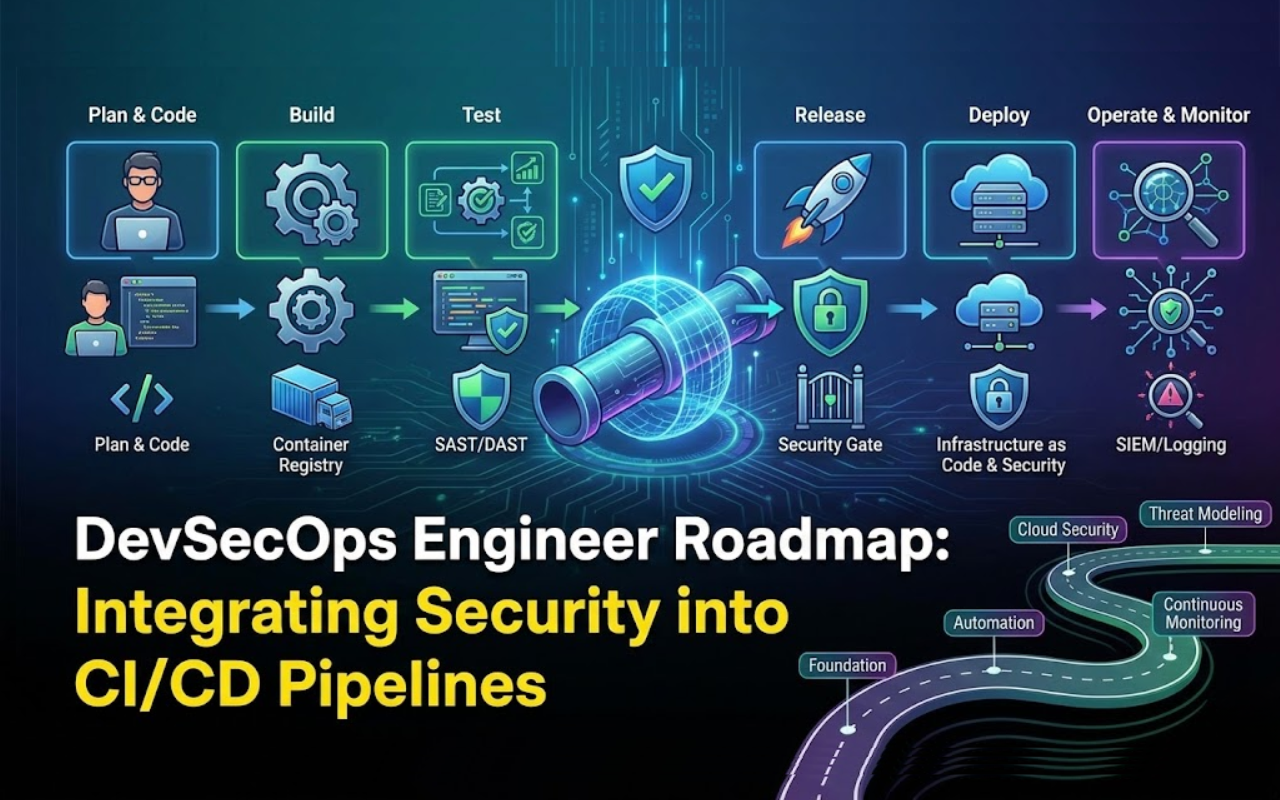
Modern software delivery is built on speed. Continuous integration and continuous deployment (CI/CD) pipelines enable teams to ship features faster than ever—but that speed also expands the attack surface. Traditional security models, where checks happen at the end of development, can no longer keep up.
This is where DevSecOps comes in.
A DevSecOps engineer embeds security directly into development and deployment workflows, ensuring vulnerabilities are identified and addressed without slowing innovation. This roadmap breaks down the core skills, tools, and practices required to integrate security into CI/CD pipelines effectively.
What Is DevSecOps?
DevSecOps is the practice of integrating security controls, testing, and governance into every phase of the software development lifecycle (SDLC). Instead of treating security as a gatekeeper, DevSecOps makes it a shared responsibility across development, operations, and security teams.
For engineers, DevSecOps means:
-
Automating security checks
-
Embedding guardrails into pipelines
-
Preventing misconfigurations before production
-
Enabling rapid, secure releases at scale
Core Responsibilities of a DevSecOps Engineer
A DevSecOps engineer sits at the intersection of engineering and security. Key responsibilities include:
-
Securing CI/CD pipelines
-
Implementing automated security testing
-
Managing secrets and credentials safely
-
Protecting containerized and cloud-native environments
-
Enforcing security policies through code
-
Monitoring production environments continuously
Roadmap to DevSecOps Expertise
1. CI/CD Pipeline Security Fundamentals
A secure pipeline is the backbone of DevSecOps.
Key skills include:
-
Securing build servers (Jenkins, GitHub Actions, GitLab CI, Azure DevOps)
-
Implementing least-privilege access for pipeline agents
-
Isolating build environments
-
Validating artifacts before promotion
-
Preventing pipeline tampering and credential leaks
Pipeline security ensures that attackers cannot inject malicious code during the build or deployment process.
2. Shift-Left Security Testing
DevSecOps emphasizes detecting issues as early as possible.
Essential tools and practices:
-
SAST (Static Application Security Testing) for source code analysis
-
DAST (Dynamic Application Security Testing) for running applications
-
SCA (Software Composition Analysis) for open-source dependencies
-
Security testing as mandatory pipeline stages
-
Fail-fast policies for critical vulnerabilities
By shifting security left, teams reduce remediation costs and prevent vulnerabilities from reaching production.
3. Infrastructure as Code (IaC) Security
Modern infrastructure is defined through code—Terraform, CloudFormation, ARM, and Kubernetes manifests.
DevSecOps engineers must master:
-
IaC scanning for misconfigurations
-
Policy-as-code using tools like OPA or Sentinel
-
Secure cloud resource provisioning
-
Preventing exposed storage, weak IAM roles, and insecure networking
IaC security ensures infrastructure is compliant, repeatable, and hardened from the start.
4. Container and Kubernetes Security
Containers accelerate deployment—but misconfigured containers are a major breach vector.
Critical container security skills include:
-
Image scanning for vulnerabilities
-
Enforcing minimal base images
-
Runtime protection and behavioral monitoring
-
Securing Kubernetes clusters (RBAC, network policies, admission controllers)
-
Detecting container escapes and privilege escalation
Container security must span build-time, deploy-time, and runtime.
5. Secrets Management and Credential Protection
Hardcoded secrets are one of the most common DevSecOps failures.
Best practices include:
-
Using centralized secrets managers (Vault, AWS Secrets Manager, Azure Key Vault)
-
Rotating credentials automatically
-
Injecting secrets securely at runtime
-
Preventing secrets from entering logs, repositories, or artifacts
Effective secrets management protects pipelines from credential theft and lateral movement.
6. Automation and Security Orchestration
DevSecOps thrives on automation.
Key automation skills:
-
Security-as-code implementation
-
Automated compliance checks
-
Security orchestration and response workflows
-
Integrating alerts with ticketing and response systems
-
Reducing manual intervention in routine security tasks
Automation enables scalability without sacrificing security assurance.
7. Monitoring, Detection, and Feedback Loops
Security does not stop at deployment.
DevSecOps engineers focus on:
-
Continuous monitoring of applications and infrastructure
-
Detecting anomalous behavior in production
-
Feeding incidents back into pipeline improvements
-
Improving security posture through metrics and lessons learned
This feedback loop drives continuous improvement across teams.
7. Monitoring, Detection, and Feedback Loops
Security does not stop at deployment.
DevSecOps engineers focus on:
-
Continuous monitoring of applications and infrastructure
-
Detecting anomalous behavior in production
-
Feeding incidents back into pipeline improvements
-
Improving security posture through metrics and lessons learned
This feedback loop drives continuous improvement across teams.
Common DevSecOps Challenges
Despite its benefits, DevSecOps adoption faces challenges:
-
Tool sprawl and integration complexity
-
Cultural resistance between teams
-
False positives slowing pipelines
-
Skill gaps across engineering and security
Successful teams address these challenges with clear ownership, training, and automation-first strategies.
The Future of DevSecOps
DevSecOps is evolving rapidly, driven by:
-
AI-powered security testing
-
Autonomous remediation
-
Zero Trust pipeline architectures
-
Increased regulatory scrutiny
-
Greater focus on developer experience
Engineers who master DevSecOps today position themselves at the center of modern security operations.
Final Thoughts
DevSecOps is no longer optional. It’s a core engineering discipline. By integrating security into CI/CD pipelines, organizations can move fast without breaking trust.
For security professionals and engineers alike, the DevSecOps roadmap is a path toward scalable, resilient, and future-ready security.